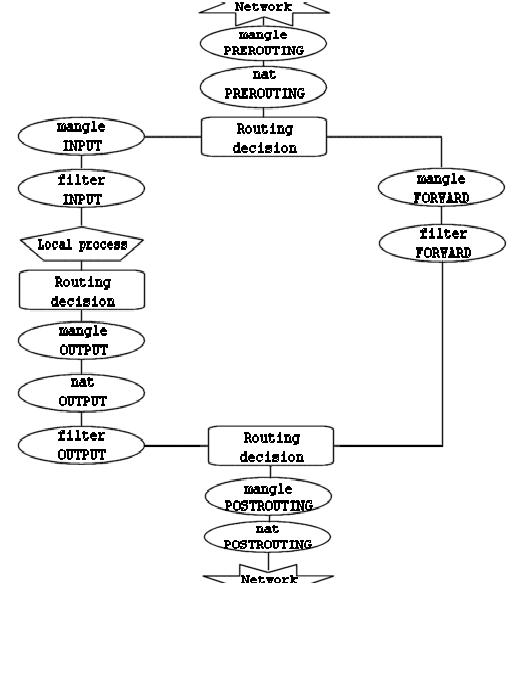
I read everywhere that it is dangerous to do traffic filtering in the nat table because the nat table is only consulted for connections whose state is "NEW" (later packets bypass the table).
Does it mean that nat table counters are only incremented for the first packet of every connection?
Should I then use the chain PREROUTING of the table RAW if I need reliable traffic information?

Best Answer
If the server is a gateway - you should use FORWARD chain
Setup iptables
We will download a simple file
Download the file
Check the rules
244733384 is what you are looking for.
It's an overhead of tcp/ip + http
yes, it does. And then it uses connection tracking
As you said before - you have 5-50 clients, so you can try do accounting through iptables and -j LOG action
Configure rsyslog
Configure iptables
Check that all works as it should
Do some real test
As you can see from the output - the client has been downloaded ~ 22,33 Mb
And now we can calculate through log file
Of course you can mix and filter sport/dport/dest ip and so on and get any statistics you want